How To Replicate Windows Server 2012
This browser is no longer supported.
Upgrade to Microsoft Edge to have advantage of the latest features, security updates, and technical support.
Install a Replica Windows Server 2012 Domain Controller in an Existing Domain (Level 200)
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
This topic covers the steps necessary to upgrade an existing woods or domain to Windows Server 2012, using either Server Manager or Windows PowerShell. It covers how to add domain controllers that run Windows Server 2012 to an existing domain.
-
Upgrade and Replica Workflow
-
Upgrade and Replica Windows PowerShell
-
Deployment
Upgrade and Replica Workflow
The following diagram illustrates the Active Directory Domain Services configuration process when y'all previously installed the AD DS role and yous have started the Active Directory Domain Services Configuration Wizard using Server Manager to create a new domain controller in an existing domain.
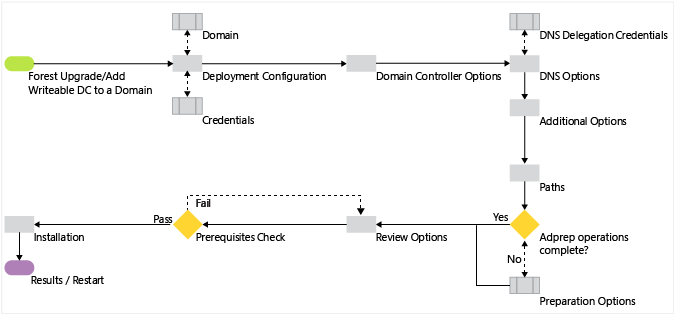
Upgrade and Replica Windows PowerShell
| ADDSDeployment Cmdlet | Arguments (Bold arguments are required. Italicized arguments tin can exist specified by using Windows PowerShell or the Advertizement DS Configuration Wizard.) |
|---|---|
| Install-AddsDomainController | -SkipPreChecks -DomainName -SafeModeAdministratorPassword -SiteName -ADPrepCredential -ApplicationPartitionsToReplicate -AllowDomainControllerReinstall -Confirm -CreateDNSDelegation -Credential -CriticalReplicationOnly -DatabasePath -DNSDelegationCredential -Strength -InstallationMediaPath -InstallDNS -LogPath -MoveInfrastructureOperationMasterRoleIfNecessary -NoDnsOnNetwork -NoGlobalCatalog -Norebootoncompletion -ReplicationSourceDC -SkipAutoConfigureDNS -SiteName -SystemKey -SYSVOLPath -UseExistingAccount -Whatif |
Note
The -credential argument is but required if you are not already logged on as a member of the Enterprise Admins and Schema Admins groups (if you are upgrading the woods) or the Domain Admins group (if you lot are calculation a new DC to an existing domain).
Deployment
Deployment Configuration
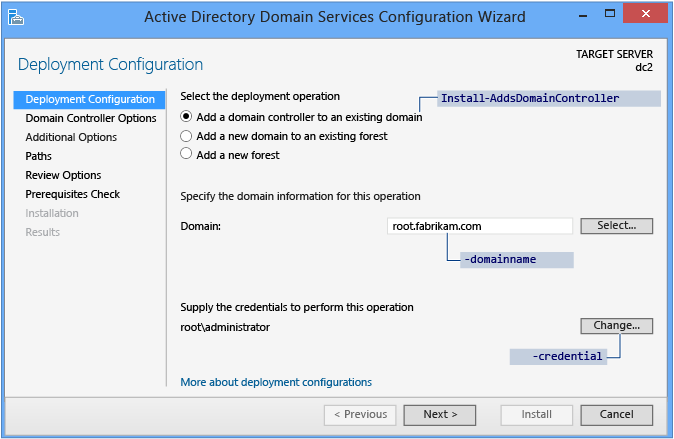
Server Manager begins every domain controller promotion with the Deployment Configuration folio. The remaining options and required fields alter on this page and subsequent pages, depending on which deployment performance yous select.
To upgrade an existing forest or add a writable domain controller to an existing domain, click Add a domain controller to an existing domain and click Select to Specify the domain information for this domain. Server Manager prompts y'all for valid credentials if needed.
Upgrading the forest requires credentials that include group memberships in both the Enterprise Admins and Schema Admins groups in Windows Server 2012. The Agile Directory Domain Services Configuration Sorcerer prompts you later on if your current credentials practise non have acceptable permissions or group memberships.
The automatic Adprep procedure is the only operational difference between adding a domain controller to an existing Windows Server 2012 domain and a domain where domain controllers run an earlier version of Windows Server.
The Deployment Configuration ADDSDeployment cmdlet and arguments are:
Install-AddsDomainController -domainname <string> -credential <pscredential> 
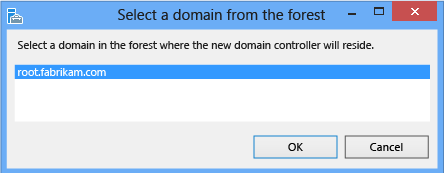
Certain tests perform at each page, some of which repeat later as detached prerequisite checks. For instance, if the selected domain does not run across the minimal functional levels, you exercise non take to become all the way through promotion to the prerequisite check to find out:

Domain Controller Options

The Domain Controller Options page specifies the domain controller capabilities for the new domain controller. The configurable domain controller capabilities are DNS server, Global Itemize, and Read-merely domain controller. Microsoft recommends that all domain controllers provide DNS and GC services for high availability in distributed environments. GC is ever selected by default and DNS server is selected by default if the current domain hosts DNS already on its DCs based on Start of Authority query. The Domain Controller Options page likewise enables you to cull the advisable Active Directory logical site proper name from the forest configuration. By default, it selects the site with the about correct subnet. If there is only one site, it selects automatically.
Note
If the server does not belong to an Active Directory subnet and there is more than one Active Directory site, aught is selected and the Next button is unavailable until y'all choose a site from the listing.
The specified Directory Services Restore Manner Countersign must adhere to the password policy applied to the server. E'er cull a strong, circuitous password or preferably, a passphrase.
The Domain Controller Options ADDSDeployment arguments are:
-InstallDNS <{$false | $true}> -NoGlobalCatalog <{$false | $true}> -sitename <string> -SafeModeAdministratorPassword <secure string> Important
The site name must already exist when provided as an argument to -sitename. The install-AddsDomainController cmdlet does non create sites. You can utilize cmdlet new-adreplicationsite to create new sites.
The SafeModeAdministratorPassword argument's performance is special:
-
If non specified as an argument, the cmdlet prompts you to enter and ostend a masked password. This is the preferred usage when running the cmdlet interactively.
For case, to create an additional domain controller in treyresearch.net domain and exist prompted to enter and ostend a masked password:
Install-ADDSDomainController "DomainName treyresearch.cyberspace "credential (get-credential) -
If specified with a value, the value must exist a secure cord. This is not the preferred usage when running the cmdlet interactively.
For example, you lot can manually prompt for a password past using the Read-Host cmdlet to prompt the user for a secure cord:
-safemodeadministratorpassword (read-host -prompt "Password:" -assecurestring) Warning
As the previous option does not confirm the password, employ farthermost caution: the password is not visible.
You tin likewise provide a secure string equally a converted clear-text variable, although this is highly discouraged.
-safemodeadministratorpassword (convertto-securestring "Password1" -asplaintext -force) Finally, yous could store the obfuscated password in a file, and so reuse information technology later, without the articulate text password ever appearing. For case:
$file = "c:\pow.txt" $pw = read-host -prompt "Password:" -assecurestring $pw | ConvertFrom-SecureString | Set-Content $file -safemodeadministratorpassword (Get-Content $File | ConvertTo-SecureString) Warning
Providing or storing a clear or obfuscated text password is not recommended. Anyone running this command in a script or looking over your shoulder knows the DSRM password of that domain controller. Anyone with admission to the file could reverse that obfuscated password. With that knowledge, they can logon to a DC started in DSRM and eventually impersonate the domain controller itself, elevating their privileges to the highest level in an Agile Directory forest. An additional gear up of steps using System.Security.Cryptography to encrypt the text file data is advisable but out of scope. The best practice is to totally avoid countersign storage.
The ADDSDeployment cmdlet offers an boosted option to skip automatic configuration of DNS client settings, forwarders, and root hints. Y'all cannot skip this configuration pick when using Server Managing director. This argument matters only if y'all installed the DNS Server office prior to configuring the domain controller:
-SkipAutoConfigureDNS The Domain Controller Options folio warns that you lot cannot create read only domain controllers if your existing domain controllers run Windows Server 2003. This is expected, and yous can dismiss the alert.

DNS Options and DNS Delegation Credentials
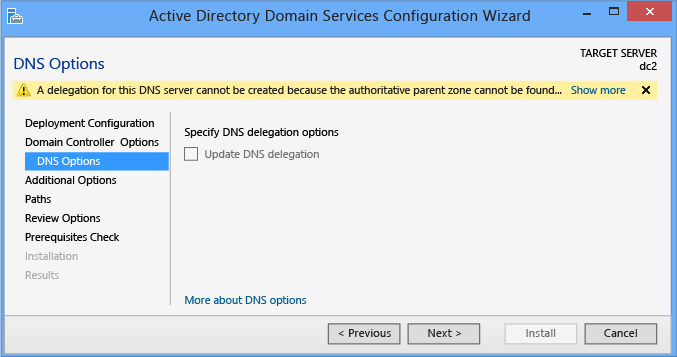
The DNS Options page enables you to configure DNS delegation if y'all selected the DNS server option on the Domain Controller Options folio and if pointing to a zone where DNS delegations are allowed. You may need to provide alternate credentials of a user that is a member of the DNS Admins grouping.
The DNS Options ADDSDeployment cmdlet arguments are:
-creatednsdelegation -dnsdelegationcredential <pscredential> 
For more information nigh whether you need to create a DNS delegation, see Agreement Zone Delegation.
Additional Options
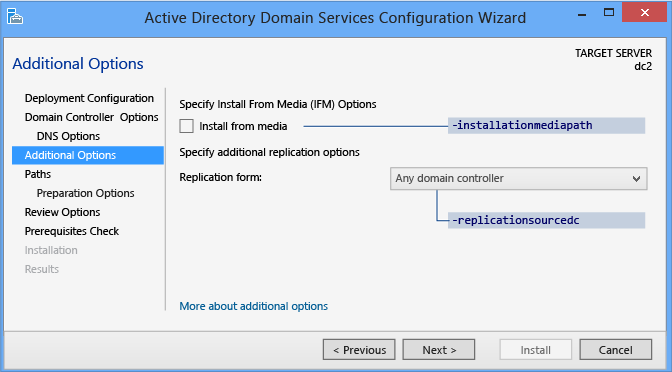
The Additional Options page provides the configuration selection to name a domain controller equally the replication source, or yous tin apply any domain controller as the replication source.
You can as well choose to install the domain controller using backed upwards media using the Install from media (IFM) choice. The Install from media checkbox provides a scan pick one time selected and you must click Verify to ensure the provided path is valid media. Media used by the IFM option is created with Windows Server Backup or Ntdsutil.exe from another existing Windows Server 2012 computer simply; yous cannot use a Windows Server 2008 R2 or previous operating organisation to create media for a Windows Server 2012 domain controller. For more information about changes in IFM, see Simplified Administration Appendix. If using media protected with a SYSKEY, Server Manager prompts for the epitome's countersign during verification.
The Additional Options ADDSDeployment cmdlet arguments are:
-replicationsourcedc <string> -installationmediapath <string> -syskey <secure cord> Paths
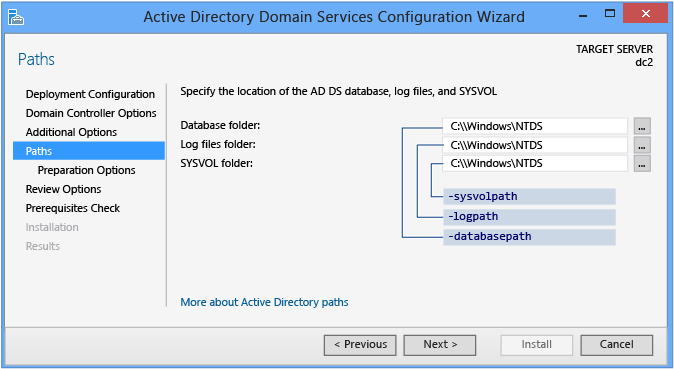
The Paths page enables you to override the default binder locations of the Advertizement DS database, the database transaction logs, and the SYSVOL share. The default locations are always in subdirectories of %systemroot%.
The Active Directory Paths ADDSDeployment cmdlet arguments are:
-databasepath <string> -logpath <string> -sysvolpath <string> Training Options

The Grooming Options page alerts you that the AD DS configuration includes extending the Schema (forestprep) and updating the domain (domainprep). You lot merely meet this page when the woods and domain have not been prepared by previous Windows Server 2012 domain controller installation or from manually running Adprep.exe. For example, the Active Directory Domain Services Configuration Magician suppresses this folio if you lot add together a new domain controller to an existing Windows Server 2012 forest root domain.
Extending the Schema and updating the domain do non occur when you click Next. These events occur only during the installation stage. This page simply brings awareness about the events that volition occur afterwards in the installation.
This folio also validates that the current user credentials are members of the Schema Admin and Enterprise Admins groups, as you lot need membership in these groups to extend the schema or prepare a domain. Click Change to provide the adequate user credentials if the page informs you that the current credentials do not provide sufficient permissions.
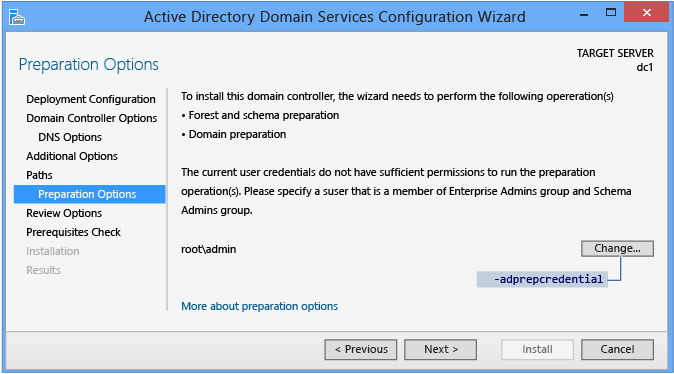
The Additional Options ADDSDeployment cmdlet argument is:
-adprepcredential <pscredential> Important
Equally with previous versions of Windows Server, automated domain preparation for domain controllers that run Windows Server 2012 does not run GPPREP. Run adprep.exe /gpprep manually for all domains that were non previously prepared for Windows Server 2003, Windows Server 2008, or Windows Server 2008 R2. You should run GPPrep merely once in the history of a domain, non with every upgrade. Adprep.exe does non run /gpprep automatically because its operation can cause all files and folders in the SYSVOL folder to re-replicate on all domain controllers.
Automatic RODCPrep runs when y'all promote the first united nations-staged RODC in a domain. Information technology does not occur when you promote the kickoff writeable Windows Server 2012 domain controller. Y'all tin too still manually adprep.exe /rodcprep if y'all plan to deploy read-only domain controllers.
Review Options and View Script

The Review Options page enables you to validate your settings and ensure that they meet your requirements earlier yous start the installation. This is not the last opportunity to end the installation using Server Managing director. This folio simply enables you to review and ostend your settings earlier continuing the configuration.
The Review Options page in Server Manager also offers an optional View Script button to create a Unicode text file that contains the current ADDSDeployment configuration as a single Windows PowerShell script. This enables you to use the Server Manager graphical interface equally a Windows PowerShell deployment studio. Use the Active Directory Domain Services Configuration Sorcerer to configure options, export the configuration, and so cancel the wizard. This procedure creates a valid and syntactically correct sample for further modification or directly use.
For instance:
# # Windows PowerShell Script for AD DS Deployment # Import-Module ADDSDeployment Install-ADDSDomainController ` -CreateDNSDelegation ` -Credential (Get-Credential) ` -CriticalReplicationOnly:$simulated ` -DatabasePath "C:\Windows\NTDS" ` -DomainName "root.fabrikam.com" ` -InstallDNS:$truthful ` -LogPath "C:\Windows\NTDS" ` -SiteName "Default-First-Site-Name" ` -SYSVOLPath "C:\Windows\SYSVOL" -Force:$true Note
Server Manager generally fills in all arguments with values when promoting and does non rely on defaults (as they may modify betwixt futurity versions of Windows or service packs). The i exception to this is the -safemodeadministratorpassword argument. To strength a confirmation prompt omit the value when running cmdlet interactively
Use the optional Whatif argument with the Install-ADDSDomainController cmdlet to review configuration information. This enables y'all to meet the explicit and implicit values of the arguments for a cmdlet.
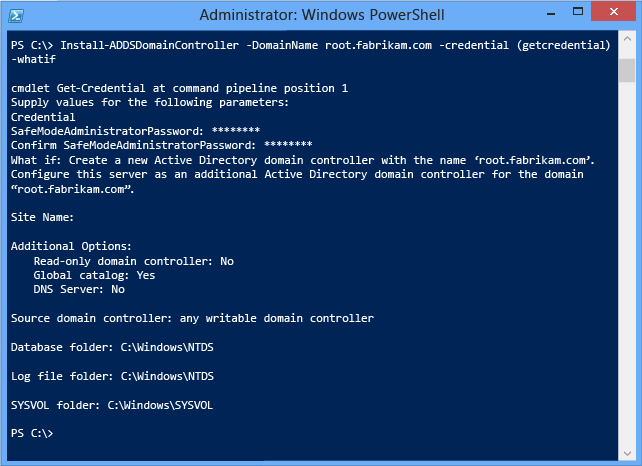
Prerequisites Bank check
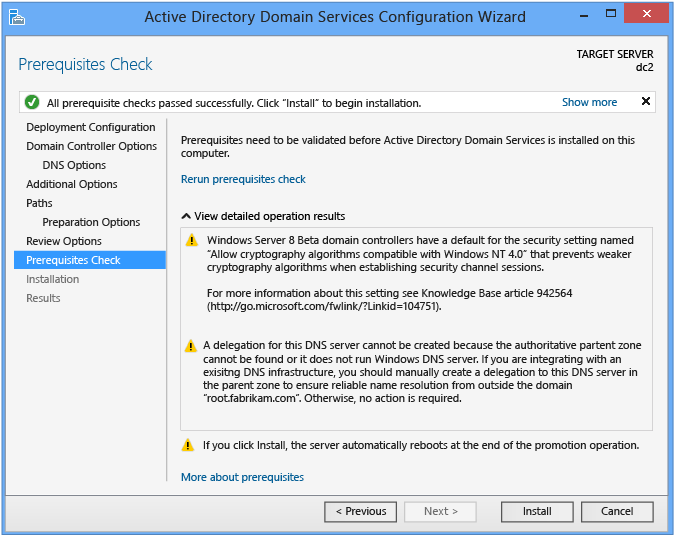
The Prerequisites Bank check is a new feature in AD DS domain configuration. This new phase validates that the domain and wood are capable of supporting a new Windows Server 2012 domain controller.
When installing a new domain controller, the Server Manager Active Directory Domain Services Configuration Sorcerer invokes a series of serialized modular tests. These tests alert yous with suggested repair options. Y'all can run the tests as many times as required. The domain controller process cannot continue until all prerequisite tests pass.
The Prerequisites Check likewise surfaces relevant information such as security changes that affect older operating systems.
For more data about the specific prerequisite checks, see Prerequisite Checking.
Y'all cannot bypass the Prerequisite Check when using Server Director, only y'all tin can skip the process when using the Advert DS Deployment cmdlet using the following argument:
-skipprechecks Warning
Microsoft discourages skipping the prerequisite check as it tin can pb to a partial domain controller promotion or damaged Advertizement DS forest.
Click Install to brainstorm the domain controller promotion process. This is last opportunity to cancel the installation. You cannot cancel the promotion process once it begins. The reckoner volition reboot automatically at the end of promotion, regardless of the promotion results.The Prerequisites Cheque page displays any issues it encountered during the process and guidance for resolving the issue.
Installation

When the Installation page displays, the domain controller configuration begins and cannot be halted or canceled. Detailed operations brandish on this page and are written to logs:
-
%systemroot%\debug\dcpromo.log
-
%systemroot%\debug\dcpromoui.log
-
%systemroot%\debug\adprep\logs
-
%systemroot%\debug\netsetup.log (if server is in a workgroup)
To install a new Agile Directory woods using the ADDSDeployment module, use the following cmdlet:
Install-addsdomaincontroller See Upgrade and Replica Windows PowerShell for required and optional arguments.
The Install-AddsDomainController cmdlet simply has two phases (prerequisite checking and installation). The two figures below show the installation phase with the minimum required arguments of -domainname and -credential. Note how the Adprep operation happens automatically as office of adding the start Windows Server 2012 domain controller to an existing Windows Server 2003 forest:
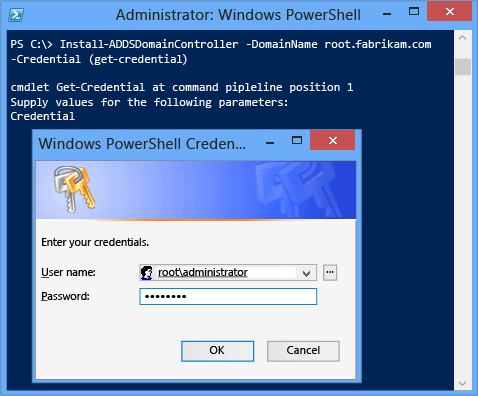
Note how, merely similar Server Manager, Install-ADDSDomainController reminds you that promotion will reboot the server automatically. To have the reboot prompt automatically, use the -force or -ostend:$simulated arguments with whatsoever ADDSDeployment Windows PowerShell cmdlet. To prevent the server from automatically rebooting at the end of promotion, use the -norebootoncompletion argument.
Alert
Overriding the reboot is discouraged. The domain controller must reboot to office correctly.


To configure a domain controller remotely using Windows PowerShell, wrap the install-addsdomaincontroller cmdlet inside of the invoke-command cmdlet. This requires using the curly braces.
invoke-command {install-addsdomaincontroller "domainname <domain> -credential (become-credential)} -computername <dc name> For example:

Results
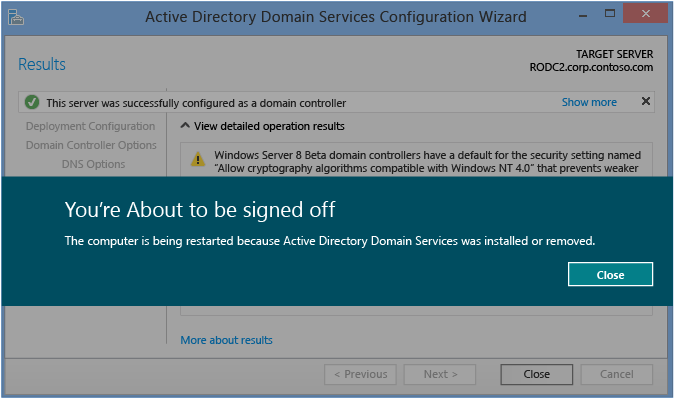
The Results folio shows the success or failure of the promotion and any important administrative information. If successful, the domain controller volition automatically reboot afterwards 10 seconds.
As with previous versions of Windows Server, automated domain preparation for domain controllers that run Windows server 2012 does not run GPPREP. Run adprep.exe /gpprep manually for all domains that were not previously prepared for Windows Server 2003, Windows Server 2008, or Windows Server 2008 R2. Y'all should run GPPrep only in one case in the history of a domain, not with every upgrade. Adprep.exe does non run /gpprep automatically because its performance can cause all files and folders in the SYSVOL folder to re-replicate on all domain controllers.
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/install-a-replica-windows-server-2012-domain-controller-in-an-existing-domain--level-200-
Posted by: szabonece2002.blogspot.com

0 Response to "How To Replicate Windows Server 2012"
Post a Comment